Qilin ransomware gang now offers a “Call Lawyer” feature to pressure victims
Security Affairs
JUNE 22, 2025
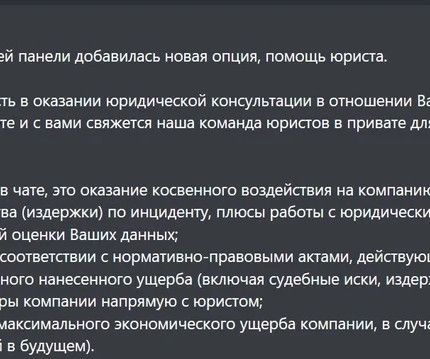
Qilin ransomware gang now offers a “Call Lawyer” feature to help affiliates pressure victims into paying, per Cybereason. The Qilin ransomware group is now offering legal support to its affiliates through a “Call Lawyer” feature to pressure victims into paying. ” reads the report published by Cybereason.














































Let's personalize your content