Breach Exposes Users of Microleaves Proxy Service
Krebs on Security
JULY 28, 2022
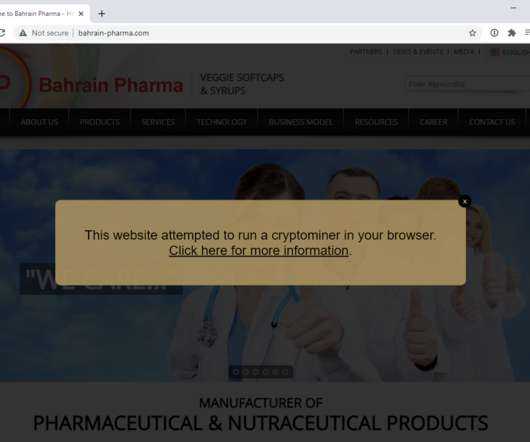
Microleaves claims its proxy software is installed with user consent, but data exposed in the breach shows the service has a lengthy history of being supplied with new proxies by affiliates incentivized to distribute the software any which way they can — such as by secretly bundling it with other titles.

























Let's personalize your content