Who and What is Behind the Malware Proxy Service SocksEscort?
Krebs on Security
JULY 25, 2023
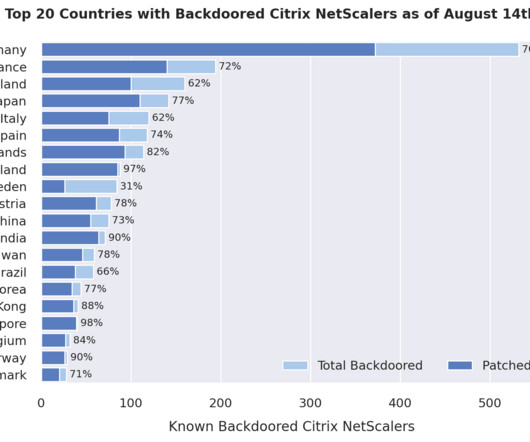
Spur tracks SocksEscort as a malware-based proxy offering, which means the machines doing the proxying of traffic for SocksEscort customers have been infected with malicious software that turns them into a traffic relay. Usually, these users have no idea their systems are compromised. co and a VPN provider called HideIPVPN[.]com.























Let's personalize your content