Using Google Search to Find Software Can Be Risky
Krebs on Security
JANUARY 25, 2024
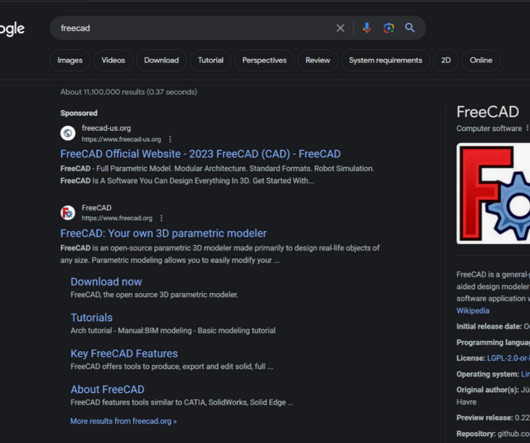
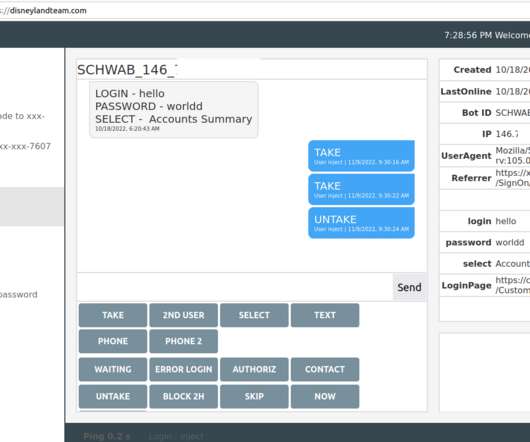
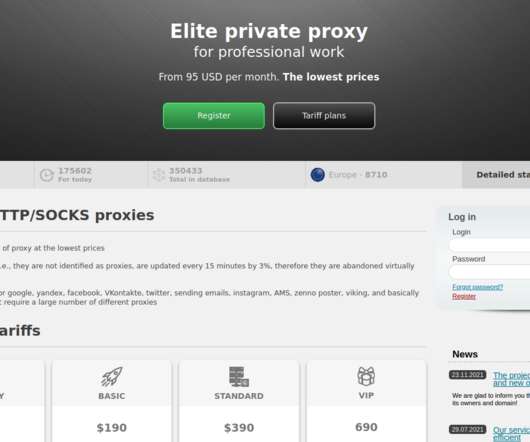
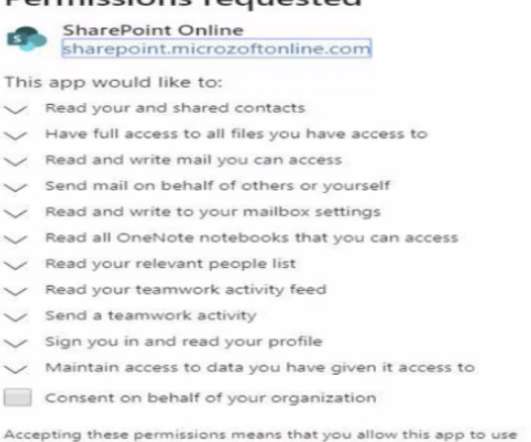
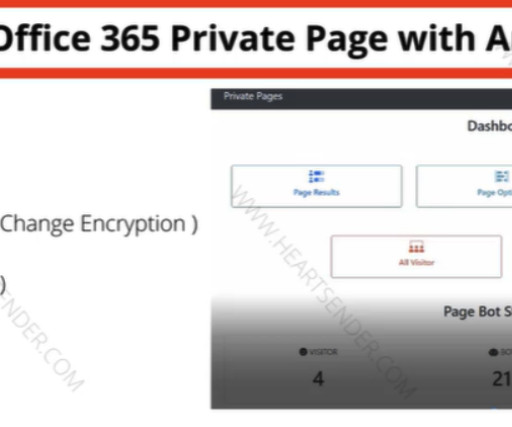
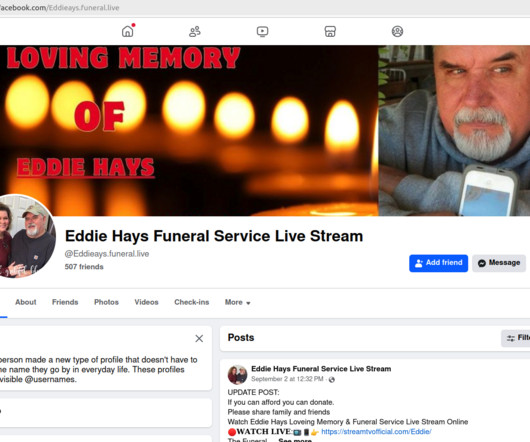
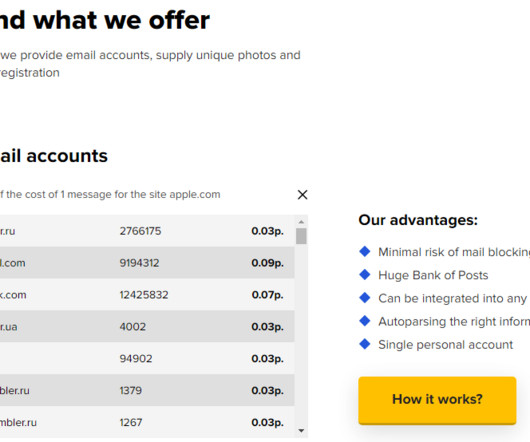
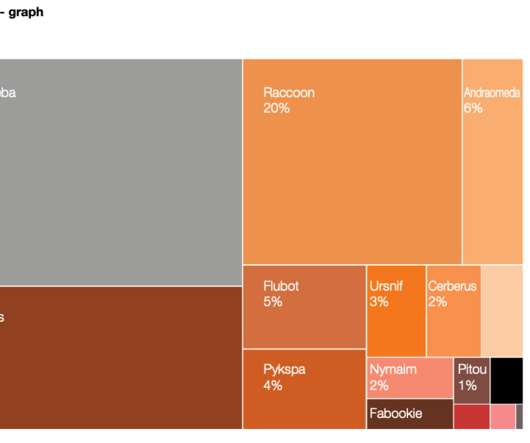
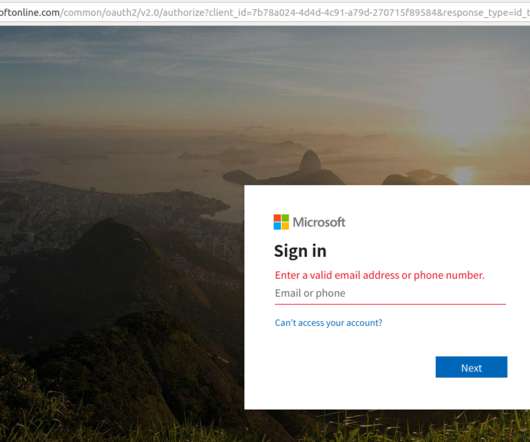
Google continues to struggle with cybercriminals running malicious ads on its search platform to trick people into downloading booby-trapped copies of popular free software applications. And by most accounts, the threat from bad ads leading to backdoored software has subsided significantly compared to a year ago. com , filezillasoft[.]com






































Let's personalize your content