How can small businesses ensure Cybersecurity?
CyberSecurity Insiders
JUNE 7, 2023
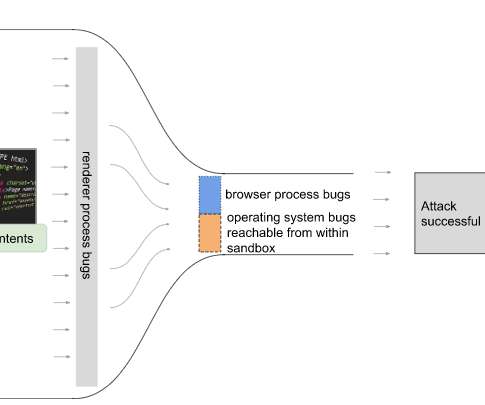
It’s also reported that state-sponsored threat actors are diversifying their tactics and shifting their focus toward smaller enterprises. Small businesses are on the target list of hackers mainly because they focus less on security. On average, SMBs and small businesses allocate 5%-20% of their total budget to security.
















Let's personalize your content