Cost-Effective Steps the Healthcare Industry Can Take To Mitigate Damaging Ransomware Attacks
CyberSecurity Insiders
OCTOBER 25, 2022
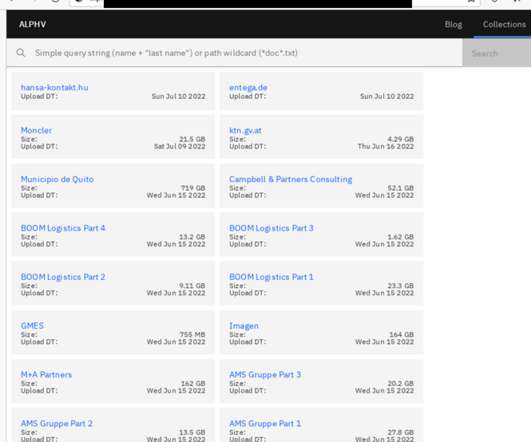
According to a recent IBM report , breaches now come with a record-high price tag of $10.1 A solid cybersecurity posture is only as strong as its policies, backups and disaster plans. million on average, leaving behind potentially disruptive damage as the industry struggles to mitigate associated costs. million patients.






















Let's personalize your content