News on WhatsApp listening to sleeping users and Doctors fraternity raising voice against AI threat to humanity
CyberSecurity Insiders
MAY 10, 2023
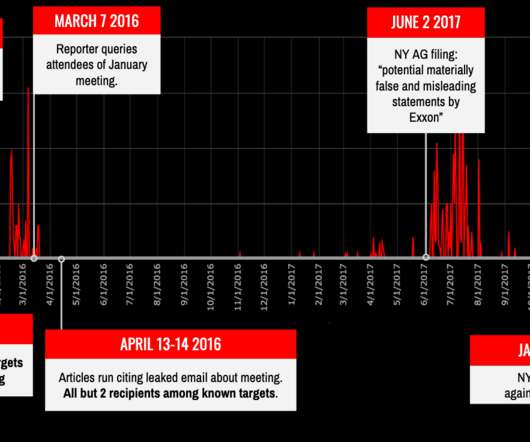
said Musk, by directly tagging the same to Facebook chief Mark Zuckerberg. Basically, they want to restrict the usage of robots in the medical field as machines cannot work with ethics like their human counterparts and can be tweaked to kill or, at the very least, influence patient minds.





















Let's personalize your content