5 Questions to Ask When Evaluating a New Cybersecurity Technology
Dark Reading
MAY 24, 2023
Any new cybersecurity technology should be not just a neutral addition to a security stack but a benefit to the other technologies or people managing them.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 technology-evaluation
technology-evaluation 
Dark Reading
MAY 24, 2023
Any new cybersecurity technology should be not just a neutral addition to a security stack but a benefit to the other technologies or people managing them.

Security Boulevard
MARCH 21, 2024
IoT producers must comprehend the relevant rules, consult legal and technological experts and evaluate cybersecurity procedures. The post IoT Consumer Labeling Goes Global – What This Means for Vendors and Consumers appeared first on Security Boulevard.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
OCTOBER 2, 2023
The NSA is starting a new artificial intelligence security center: The AI security center’s establishment follows an NSA study that identified securing AI models from theft and sabotage as a major national security challenge, especially as generative AI technologies emerge with immense transformative potential for both good and evil.

Security Boulevard
MAY 13, 2024
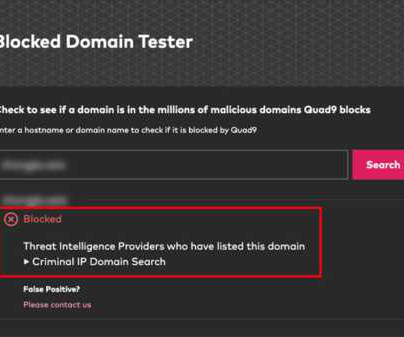
Torrance, California, May 13th, 2024, CyberNewsWire Criminal IP, a renowned Cyber Threat Intelligence (CTI) search engine developed by AI SPERA, has recently signed a technology partnership to exchange threat intelligence data based on domains and potentially on the IP address to protect users by blocking threats to end users.

Schneier on Security
JUNE 23, 2022
National Institute of Standards and Technology (NIST), which develops cryptographic standards for non-national security agencies of the U.S. Cryptographic algorithms are essential to security yet are hard to understand and evaluate. These technologies provide crucial security for communications protocols.

CSO Magazine
MAY 31, 2022
federal government introduced a proposed five-step 5G Security Evaluation Process Investigation. “[It] It] was developed to address gaps in existing security assessment guidance and standards that arise from the new features and services in 5G technologies," Eric Goldstein, executive assistant director for the U.S. Last week the U.S.

Tech Republic Security
DECEMBER 3, 2023
“The security technology market is in a state of general overload with pressure on budgets, staff hiring/retention, and having too many point solutions are pervasive issues for organizations today.”

Security Boulevard
APRIL 23, 2024
Overview The release of the National Institute of Standards and Technology (NIST)’s AI Risk Management Framework (AI RMF) helped put a framework around how testing would enable organizations to manage and mitigate AI risks.

NetSpi Executives
FEBRUARY 21, 2024
Like many technologies that came before it, AI is advancing faster than security standards can keep up with. How will the model be evaluated for robustness? Before deployment, it’s crucial to have an evaluation plan in place. Having a clear evaluation plan can ensure that defenses are systematically checked and optimized.

The Last Watchdog
SEPTEMBER 25, 2023
Taking an active role Your cybersecurity policy should address your employees and technology systems. Taurins It’s also essential your business evaluates its technology and keeps it regularly updated to the latest security standards. Security places a crucial role in your technology. Employee training is crucial.

The Last Watchdog
NOVEMBER 7, 2023
AppMap’s first CI release, their new GitHub Action, brings instant insights to developers where they evaluate code quality: in the pull request. AppMap’s users liken it to a robot software “architect” that evaluates and explains every permutation of a code change on the code’s runtime behavior.

Security Boulevard
JANUARY 9, 2024
The company has announced its Vulnerability Impact Scoring System (VISS) , a free-to-use framework for evaluating the impact of security vulnerabilities on computer systems infrastructure, technology stacks, and protected data. The post Zoom joins the vulnerability fray: Will VISS move the needle on AppSec?
The Last Watchdog
MAY 13, 2024
May 13, 2024, CyberNewsWire — Criminal IP, a renowned Cyber Threat Intelligence (CTI) search engine developed by AI SPERA, has recently signed a technology partnership to exchange threat intelligence data based on domains and potentially on the IP address to protect users by blocking threats to end users. Torrance, Calif.,

eSecurity Planet
NOVEMBER 22, 2021
MITRE is moving beyond its well-regarded endpoint security evaluations and will soon be testing other security services and products. ” The services evaluation will be focused entirely on understanding adversary activity, and remediation/prevention will be prohibited, the call for participation said. Testing Deception.
InfoWorld on Security
DECEMBER 8, 2023
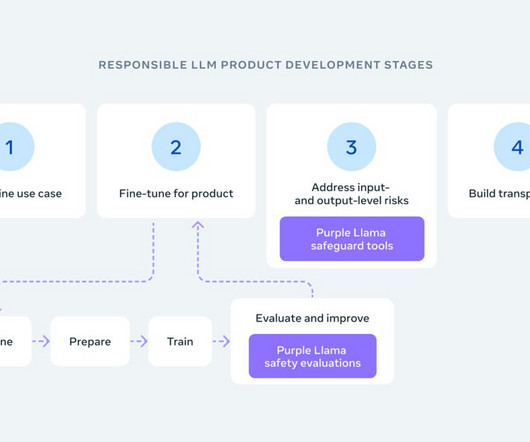
Meta has introduced Purple Llama, a project dedicated to creating open-source tools for developers to evaluate and boost the trustworthiness and safety of generative AI models before they are used publicly. Meta emphasized the need for collaborative efforts in ensuring AI safety, stating that AI challenges cannot be tackled in isolation.

CSO Magazine
MAY 2, 2023
The White House Office of Science and Technology Policy (OSTP) would soon be releasing a public request for information (RFI) to learn more about the automated tools employers use to surveil, monitor, evaluate, and manage workers, OSTP announced on Monday. To read this article in full, please click here

Security Affairs
JULY 1, 2021
The US Cybersecurity and Infrastructure Security Agency (CISA) has released the Ransomware Readiness Assessment (RRA) , a new ransomware self-assessment security audit tool for the agency’s Cyber Security Evaluation Tool ( CSET ). ” CISA says.

Security Boulevard
NOVEMBER 2, 2022
A recent Cloud Native Computing Foundation (CNCF) survey showed that 96% of respondents were using or evaluating Kubernetes and 93% of respondents are using containers in production environments. And it’s not only emerging companies adopting these technologies, but large companies as well – frequently even more than smaller ones.

Schneier on Security
MARCH 23, 2022
However, on-going concerns including staffing challenges, technology resource limitations, and lack of funding to support such an expansion would need to be addressed prior to enhancing the existing program. Further amplifying the complexities of insider threats are the cross-discipline challenges surrounding cybersecurity expertise.

CSO Magazine
APRIL 11, 2022
Like any digital technology, AI can suffer from a range of traditional security weaknesses and other emerging concerns such as privacy, bias, inequality, and safety issues. To read this article in full, please click here

NetSpi Executives
JANUARY 30, 2024
What to Look for When Evaluating External Attack Surface Management Providers To simplify the process of evaluating attack surface management vendors, we’ve identified five important criteria to look for when comparing different companies.

Digital Guardian
MAY 3, 2021
To reduce malicious cyberattacks against operational technology (OT) following last year's SolarWinds attack, the National Security Agency has released evaluation methodology for network owners.

Security Affairs
DECEMBER 8, 2020
The Apache Software Foundation addressed a possible remote code execution vulnerability in Struts 2 related to the OGNL technology. . The Apache Software Foundation has released a security update to address a “possible remote code execution” flaw in Struts 2 that is related to the OGNL technology. . The flaw affects Struts 2.0.0

CSO Magazine
MARCH 28, 2023
An effective CISO has the ability to evaluate and select security technology, communicate with technical staff and make crucial decisions about security infrastructure and architecture. Technical expertise and experience are obviously huge assets.

Dark Reading
JUNE 16, 2022
Security pros can employ the technology to evaluate vulnerabilities and system capabilities, but they need to watch for the potential risks.
The Hacker News
JULY 28, 2022
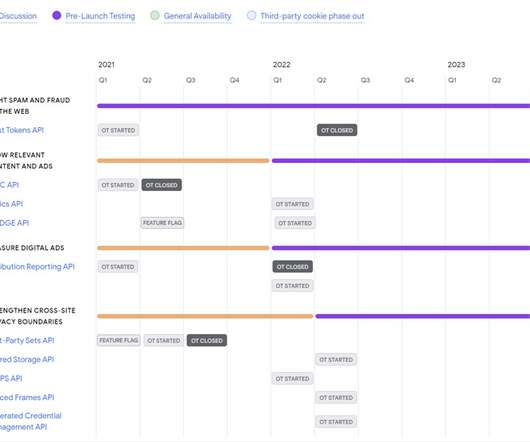
The most consistent feedback we've received is the need for more time to evaluate and test the new Privacy Sandbox technologies before deprecating third-party cookies in Chrome," Anthony Chavez, vice president of Privacy Sandbox, said.

Hacker's King
JUNE 30, 2023
The Chief Technology Officer (CTO) is a key executive who plays a crucial role in managing technology within an organization. The role of a Chief Technology Officer (CTO) has become increasingly vital in today’s technology-driven business landscape.

Centraleyes
MARCH 3, 2024
What : Clearly define regulatory requirements, industry standards, and internal policies to establish a foundation for evaluating risks. How : Evaluate compliance risk assessment methodologies and tools for efficient risk identification, evaluation, and mitigation, incorporating technological advancements and best practices.

TrustArc
MAY 31, 2023
TrustArc’s Assessment Manager gives companies automated tools and a powerful risk management framework to help privacy and security professionals evaluate third-party vendor risk. The post Privacy Technology Brief: Managing Third-Party Vendor Risk with TrustArc appeared first on TrustArc Privacy Blog.

Dark Reading
APRIL 13, 2022
In this webinar replay, Omdia outlines the ways in which XDR facilitates faster and easier threat detection and response, and key points organizations should consider when evaluating XDR technology.

CSO Magazine
FEBRUARY 1, 2023
The Open Software Supply Chain Attack Reference (OSC&R) initiative, led by OX Security, evaluates software supply chain security threats, covering a wide range of attack vectors including vulnerabilities in third-party libraries and components, supply chain attacks on build and deployment systems, and compromised or malicious software updates.

SecureBlitz
SEPTEMBER 19, 2022
Do you know what technology stack is right for your project & budget? That’s a trick question to answer…Most people feel they should first evaluate what technology stack their project requires, right? But then they get confused about which technology stack must be used.

CyberSecurity Insiders
APRIL 5, 2023
An ethics group that specializes in technology has lodged a complaint against OpenAI, the de-veloper of ChatGPT, with the Federal Trade Commission (FTC). The FTC has yet to respond to the complaint, but has stated that the usage of AI technology should be transparent and foster liability.

Schneier on Security
DECEMBER 19, 2023
This isn’t helped by the fact that AI technology means the scope of what’s possible is changing at a rate that’s hard to appreciate even if you’re deeply aware of the space. How many more turned off that AI toggle, ruling out ever evaluating if those features were useful for them or not?
Krebs on Security
OCTOBER 22, 2020
Technology Inc. Technology Inc. Technology gives the latter the right to use more than 21,500 IP addresses. Technology’s listing in the Nevada Secretary of State records. Technology’s listing in the Nevada Secretary of State records. Technology responded to repeated requests for comment.

Cisco Security
JANUARY 18, 2023
When EMA asked many of the same questions in an updated survey of 204 technology and business leaders toward the end of 2022, they found that nearly all the conclusions in the 2018/2019 report still hold true today. for no other reason than existing technologies being depreciated – but that continues to be a slow process.

Tech Republic Security
APRIL 26, 2023
As a pure-play technology, Security Orchestration, Automation and Response (SOAR) Solutions continues to mature, but remains a relatively niche market. Security and risk management leaders should evaluate how SOAR can support and optimize their broader security operations capabilities.

Security Boulevard
APRIL 19, 2024
Security testing allows you to evaluate the robustness of applications and systems and identify potential weaknesses that attackers may exploit. Fuzz is also a form of dynamic testing and can be seen as a form of DAST with its own specific technology of testing.

CSO Magazine
APRIL 3, 2023
M&A teams are generally limited in size and focused on financials and business operations, with IT and cybersecurity taking a back seat early in the process, according to Doug Saylors, partner and co-lead of cybersecurity with global technology research and advisory firm ISG.

eSecurity Planet
NOVEMBER 25, 2020
Encryption remains a mainstay of IT security technology, a critical tool for protecting sensitive data. We evaluate the top encryption solutions.

Heimadal Security
MAY 6, 2022
In reply to EO (Executive Order) 14028 promulgated on the 12th of May 2021, the National Institute of Standards and Technology (NIST) has released a comprehensive guide on how institutions can protect themselves against supply chain attacks & compromise.

CSO Magazine
NOVEMBER 17, 2021
Any small businesses that does not have an automated way to investigate intrusions and other security issues, or any sort of endpoint detection and response (EDR) technology in place should evaluate it. So should managed service providers that support small business or have connections to a small business that supplies to your firm.

CSO Magazine
JUNE 2, 2022
The platform, Arculix, combines orchestration, passwordless technology and continuous authentication and can be deployed out of the box with any industry-standard identity provider as an end-to-end solution or as augmentation to an existing identity and access management (IAM) scheme. To read this article in full, please click here

Malwarebytes
MARCH 13, 2024
The AVLab Assessment AVLabs evaluation process is extensive and comprehensive, putting cybersecurity products through a rigorous series of real-world scenarios. ThreatDown has once again earned a perfect score in AVLabs’ January 2024 real-world malware detection tests, marking the eleventh consecutive quarter in achieving this feat.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content