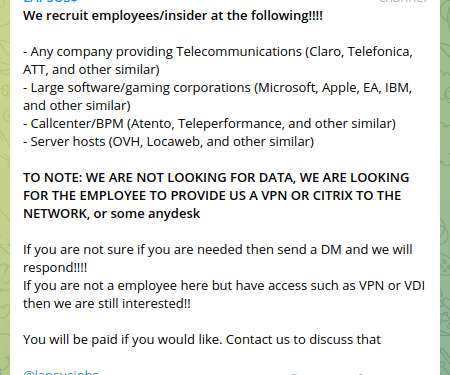
Lapsus$ Ransomware Group is hiring, it announced recruitment of insiders
Security Affairs
MARCH 11, 2022
Their scope of interests include – major telecommunications companies such as Claro, Telefonica and AT&T. ” – said Christian Lees, CTO of Resecurity, Inc, a Los Angeles-based cybersecurity company providing managed threat detection and response.
























Let's personalize your content