MasterCard DNS Error Went Unnoticed for Years
Krebs on Security
JANUARY 22, 2025
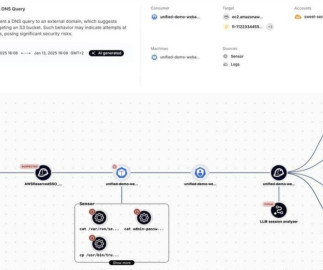
The payment card giant MasterCard just fixed a glaring error in its domain name server settings that could have allowed anyone to intercept or divert Internet traffic for the company by registering an unused domain name. The misconfiguration persisted for nearly five years until a security researcher spent $300 to register the domain and prevent it from being grabbed by cybercriminals.













Let's personalize your content