Understanding ransomware trends to combat threats
CyberSecurity Insiders
AUGUST 17, 2022
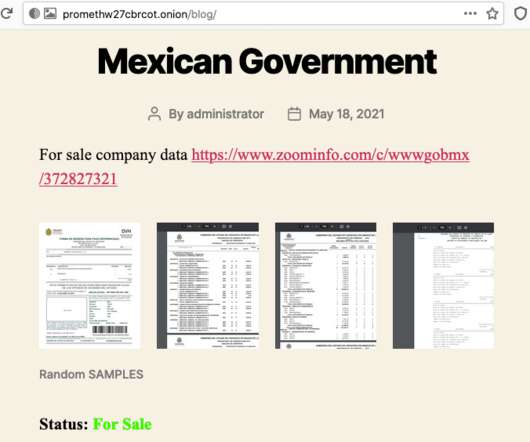
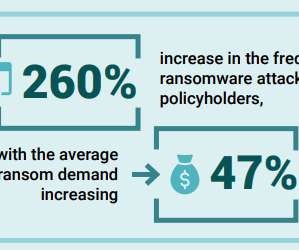
It should be no surprise that ransomware is currently one of the most common attack vectors wreaking havoc on businesses worldwide. Attackers and ransomware operators are constantly looking for more vulnerabilities to weaponize and increase their arsenal of tools, tactics, and techniques. How to use data to combat ransomware.


























Let's personalize your content