VMware Flaw a Vector in SolarWinds Breach?
Krebs on Security
DECEMBER 18, 2020
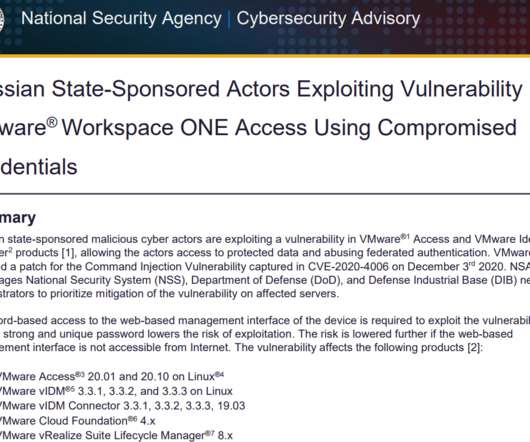
The NSA said that in order to exploit this particular flaw, hackers would already need to have access to a vulnerable VMware device’s management interface — i.e., they would need to be on the target’s internal network (provided the vulnerable VMware interface was not accessible from the Internet).














Let's personalize your content