FBI’s investigation accidentally revealed the HelloKitty ransomware gang operates out of Ukraine
Security Affairs
DECEMBER 15, 2021
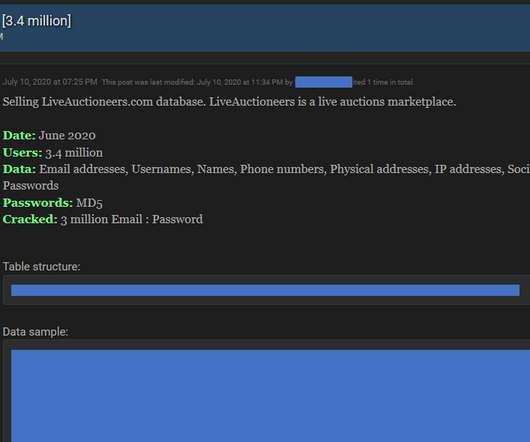
While investigating a data breach suffered by a healthcare organization, FBI accidentally revealed that it believes that the HelloKitty ransomware gang operates out of Ukraine. ” reads the notice of data breach published by the Oregon Anesthesiology Group. “Oregon Anesthesiology Group, P.C.






















Let's personalize your content