New Attack on VPNs
Schneier on Security
MAY 7, 2024
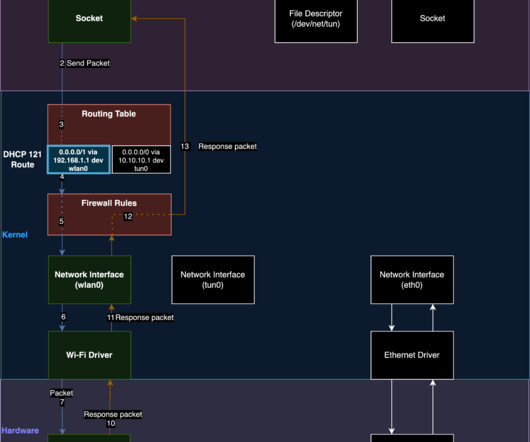
This attack has been feasible for over two decades: Researchers have devised an attack against nearly all virtual private network applications that forces them to send and receive some or all traffic outside of the encrypted tunnel designed to protect it from snooping or tampering.






























Let's personalize your content