A Trippy Visualization Charts the Internet's Growth
WIRED Threat Level
FEBRUARY 21, 2021
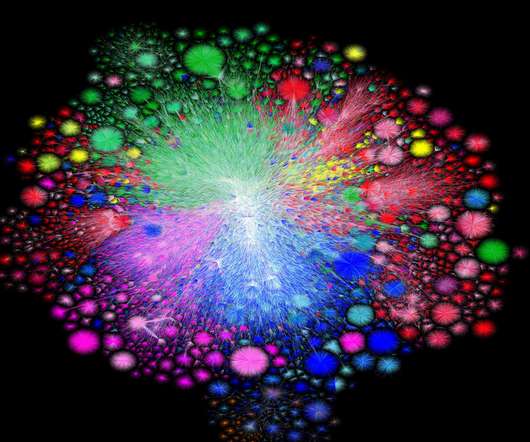
In 2003, Barrett Lyon created a map of the internet. In 2021, he did it again—and showed just how quickly it's expanded.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
WIRED Threat Level
FEBRUARY 21, 2021
In 2003, Barrett Lyon created a map of the internet. In 2021, he did it again—and showed just how quickly it's expanded.

Veracode Security
SEPTEMBER 10, 2021
Back in the summer of 2003, the internet was plagued with worms such as Blaster and Sobig. The problems I spoke of in 2003, sadly, are still here with us 18 years later. In my 2003 testimony, I said, “The current flawed computing infrastructure is not going to change for the better overnight.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
APRIL 2, 2024
Through a 2010 FOIA request (yes, it took that long), we have copies of the NSA’s KRYPTOS Society Newsletter, “ Tales of the Krypt ,” from 1994 to 2003. Schneier has gathered academic research, internet gossip, and everything he could find on cryptography into one 600-page jumble. There are many redactions.

Krebs on Security
JULY 23, 2020
had exposed approximately 885 million records related to mortgage deals going back to 2003. In May 2019, KrebsOnSecurity broke the news that the website of mortgage title insurance giant First American Financial Corp.
Krebs on Security
JULY 31, 2024
Your Web browser knows how to find a site like example.com thanks to the global Domain Name System (DNS), which serves as a kind of phone book for the Internet by translating human-friendly website names (example.com) into numeric Internet addresses. com , which was initially registered on behalf of CBS Interactive Inc.

The Last Watchdog
JUNE 9, 2022
And, let’s be honest , the deceptive writing phishing assaults and other cyber threats today employ are skilled enough to fool even the most trained, internet-savvy experts. Internet and email fraud. He has been a member of the California State Bar since 2003. Ever present threats.

Security Affairs
MAY 28, 2019
GreyNoise is observing sweeping tests for systems vulnerable to the RDP "BlueKeep" (CVE-2019-0708) vulnerability from several dozen hosts around the Internet. Microsoft has released patches for Windows 7, Server 2008, XP and Server 2003. Now the popular expert Robert Graham has scanned the Internet for vulnerable systems.

Malwarebytes
JUNE 15, 2022
Today, the Internet Explorer (IE) 11 desktop application goes out of support and will be retired for certain versions of Windows 10. Microsoft’s Internet Explorer 1.0 With Windows 10, Edge became the default Microsoft browser, but Internet Explorer could still be found in the Windows Accessories folder. Not so much.

Krebs on Security
JUNE 29, 2023
In March 2020, the DOJ unsealed two criminal hacking indictments against Kislitsin, who was then head of security at Group-IB , a cybersecurity company that was founded in Russia in 2003 and operated there for more than a decade before relocating to Singapore.

Krebs on Security
JANUARY 8, 2024
For example, in 2010 Spamdot and its spam affiliate program Spamit were hacked, and its user database shows Sal and Icamis often accessed the forum from the same Internet address — usually from Cherepovets , an industrial town situated approximately 230 miles north of Moscow. And there were many good reasons to support this conclusion.

Veracode Security
MAY 18, 2023
It’s been twenty-five years since our group of hackers (or vulnerability researchers, if you will) stepped up to raise awareness about the importance of internet security in front of some of the world’s most powerful lawmakers. Even my 2003 testimony to Congress still proved that we have a long way to go in building secure software.

Security Boulevard
SEPTEMBER 10, 2021
Back in the summer of 2003, the internet was plagued with worms such as Blaster and Sobig. The problems I spoke of in 2003, sadly, are still here with us 18 years later. In my 2003 testimony, I said, “The current flawed computing infrastructure is not going to change for the better overnight.

Schneier on Security
SEPTEMBER 30, 2019
Sometimes we can do this for some classes of back doors: We can inspect source code this is how a Linux back door was discovered and removed in 2003 or the hardware design, which becomes a cleverness battle between attacker and defender. These are research projects on a par with the internet itself.

Heimadal Security
SEPTEMBER 21, 2021
The Internet Information Services (IIS) is Microsoft Windows web server software included with all Windows versions since Windows 2000, XP, and Server 2003. Windows IIS servers were compromised by threat actors to add expired certificate notification pages asking visitors to download a malicious fake installer.

Penetration Testing
JUNE 22, 2024
The flaw, designated CVE-2024-2003 (CVSS 7.3) ESET, a leading cybersecurity provider, has addressed a high-severity vulnerability in its range of Windows security products.

Security Affairs
AUGUST 17, 2021
A security researcher discovered that a secret FBI’s terrorist watchlist was accidentally exposed on the internet for three weeks between July 19 and August 9, 2021. million records that were exposed on the internet for three weeks between July 19 and August 9, 2021. In any case, any thoughts as of where to responsibly report?

McAfee
FEBRUARY 17, 2021
Use of “domain age” is a feature being promoted by various firewall and web security vendors as a method to protect users and systems from accessing malicious internet destinations. The sites and domains of the internet are constantly changing and evolving. The domain airnigeria.com was originally registered in 2003.

Veracode Security
SEPTEMBER 10, 2021
Back in the summer of 2003, the internet was plagued with worms such as Blaster and Sobig. This time I testified as a cybersecurity professional using my real name. I was the director of research and development at @stake, an information security consulting company. Why had 400,000 computers been infected with Blaster in…

Security Affairs
MAY 31, 2019
Microsoft has released patches for Windows 7, Server 2008, XP and Server 2003. Recently, the popular expert Robert Graham has scanned the Internet for vulnerable systems. ” Microsoft also pointed out that workstations not connected to the Internet are also exposed to the risk of a hack.

The Last Watchdog
SEPTEMBER 16, 2019
Related: The case for ‘zero trust’ There’s no disputing that blockchain technology holds the potential to massively disrupt business, politics and culture over the next couple of decades, much the way the Internet dramatically altered the world over the first two decades of this century. I’ll keep these conversations going.

Herjavec Group
AUGUST 26, 2021
1988 — The Morris Worm — Robert Morris creates what would be known as the first worm on the Internet. After being released in 2003, he uses WiFi to commit attacks, program malware and steal credit card information. 2003 — Operation CyberSweep — The U.S. 1998-2007 — Max Butler — Max Butler hacks U.S.

Security Affairs
JUNE 5, 2019
Microsoft has released patches for Windows 7, Server 2008, XP and Server 2003. In addition to installing the patches from Microsoft, Windows users can mitigate attacks: Block TCP Port 3389 at your firewalls, especially any perimeter firewalls exposed to the internet. Enable Network Level Authentication.

Security Affairs
JULY 15, 2020
on the CVSS scale and affects Windows Server versions 2003 to 2019. The most severe issue is the 17-year-old wormable issue SigRed , tracked as CVE-2020-1350 , that allows hijacking of Microsoft Windows Server. The issue received a severity rating of 10.0
Security Affairs
MARCH 14, 2022
According to reports, in 2003, as deputy head of the presidential administration, he was a co-initiator of the legal prosecution and ultimately the breakup of what was once the largest oil company, Yukos.” . “Ex-Chancellor Gerhard Schröder is the chairman of the board of directors of Rosneft in Russia. ” reported Anonleaks.

The Last Watchdog
MAY 3, 2024
On January 15, 2002, Bill Gates issued his famous “ Trustworthy Computing ” (TC) company-wide memo, slamming the brakes on Windows Server 2003 development and temporarily redirecting his top engineers to emphasize security as a top priority. The common denominator is trust—critical then and now. I’ll keep watch and keep reporting.

Security Affairs
NOVEMBER 3, 2019
Microsoft has released patches for Windows 7, Server 2008, XP and Server 2003. After the disclosure of the flaw, the popular expert Robert Graham scanned the Internet for vulnerable systems. He discovered more than 923,000 potentially vulnerable devices using the masscan port scanner and a modified version of rdpscan , .

Security Affairs
MAY 15, 2019
Microsoft Patch Tuesday updates for May 2019 also address vulnerabilities in Windows OS, Internet Explorer, Edge, Microsoft Office, and Microsoft Office Services and Web Apps, ChakraCore,NET Framework, and ASP.NET, Skype for Android, Azure DevOps Server, and the NuGet Package Manager.
Security Affairs
JANUARY 24, 2023
No Fly List exposed on the Internet, the sensitive data were hosted on a server run by US airline CommuteAir. million records that were exposed on the internet for three weeks between July 19 and August 9, 2021. A researcher discovered a U.S. Researchers Maia Arson Crimew discovered a U.S.

Security Affairs
AUGUST 14, 2019
The list of flaws addressed by the tech giant doesn’t include zero-days or publicly disclosed vulnerabilities, 29 issues were rated as ‘Critical’ and affect Microsoft’s Edge and Internet Explorer web browsers, Windows, Outlook and Office. Windows XP, Windows Server 2003, and Windows Server 2008 are not affected.
Malwarebytes
MAY 12, 2021
Where vulnerable systems are accessible from the Internet, network worms can spread around the world in a matter of minutes or hours. In 2003, the infamous SQL Slammer worm infected all 75,000 its global, Internet-accessible victims within ten minutes of the attack starting. Critical issues.

The Last Watchdog
MAY 22, 2024
Mellen Mellen: The companies have dramatically different company cultures and processes, as LogRhythm is a veteran security companyfounded in 2003 with a focus on a suite-style offering, while Exabeam is, by comparison, a younger company founded in 2012 with a focus on modular, stand-alone products.

Security Affairs
SEPTEMBER 1, 2023
By scanning a range of IP addresses, they can identify potential targets that have SMB services exposed to the internet. The image below shows prebuilt EternalBlue exploits Cybernews screenshot Shodan and Similar Tools: Shodan is a search engine that scans and indexes internet-connected devices, including vulnerable systems.

eSecurity Planet
FEBRUARY 25, 2022
Read more : Best Internet Security Suites & Software. In 2003, Swiss computer scientist Phillppe Oechslin published Making a Faster Cryptanalytic Time-Memory Trade-Off , building off of Hellman and Rivest’s original application to develop what we know today as rainbow tables. Common Types of Cryptanalytic Attacks.

SecureList
APRIL 11, 2023
CLFS is a log file subsystem that was first introduced in Microsoft Windows Server 2003 R2 / Microsoft Vista and is implemented in the clfs.sys driver. We will continue to improve defenses for our users by enhancing technologies and working with third-party vendors to patch vulnerabilities, making the internet more secure for everyone.

eSecurity Planet
APRIL 5, 2023
Users, guests and internet-of-things (IoT) devices can be located, on-boarded, authenticated, and evaluated for compliance. The ExtremeControl Assessment Agent requires minimum hardware capabilities for Windows and macOS: WIndows Versions: Vista, XP, 2008, 2003, 7, 8, 8.1,

Security Boulevard
APRIL 7, 2021
This memo provides information for the Internet community. not specify an Internet standard of any kind. Copyright (C) The Internet Society (2005). values within the Internet and attempts to retrofit a suitable moral. Internet-Drafts to include a "Morality Considerations" section, and. the Internet.

SecureList
OCTOBER 4, 2022
In our case, a link to a malicious Tor installer was posted on a popular Chinese-language YouTube channel devoted to anonymity on the internet. Visual Studio 2003 – 7.10 As the Tor Browser website is blocked in China, individuals from this country often resort to downloading Tor from third-party websites. 2021-Sep-25 21:56:47.

Security Affairs
MARCH 2, 2019
This technology is stored in the Workbook OLE stream in Excel 97-2003 format which makes it very difficult to detect and parse by antivirus (AV) engines. An important point to note in “Root Entry” is the version of the document “ Microsoft Excel 97-2003 “. Figure 5: Microsoft Excel 97-2003 version identified. macro technology.

Kali Linux
APRIL 26, 2015
Once openvas-setup completes its process, the OpenVAS manager, scanner, and GSAD services should be listening: root@kali:~# netstat -antp Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 127.0.0.1:9390 [i] Online information about this feed: '[link].

eSecurity Planet
AUGUST 13, 2021
Available as a free and open-source tool, Xplico’s primary objective is to extract application data from an internet traffic capture. Started in 2003 out of Boulder, Colorado, LogRhythm’s first focus and flagship product was their SIEM software. Xplico’s supported protocols include HTTP, IMAP, POP, SMTP, IPv6, and more.

eSecurity Planet
APRIL 26, 2022
Company Sector Year Status Abnormal Security Cloud email security 2019 Private Sqreen Application security 2019 Acquired: Datadog Demisto SOAR 2018 Acquired by PAN Skyhigh Cloud security 2012 Acquired: McAfee OpenDNS Internet security 2009 Acquired: Cisco Palo Alto Networks Cloud and network security 2006 NYSE: PANW. Insight Partners.

The Security Ledger
AUGUST 16, 2019
Since then, attacks on Internet of Things devices have grown rapidly. On the Internet of Things, however, things are different. How bad is it on the Internet of Things? In all, more than 6,000 firmware versions were analyzed, totaling close to 3 million binaries created from 2003 to 2018. It has been hard to say.
SiteLock
AUGUST 27, 2021
It’s safe to say that without them, WordPress wouldn’t have grown to power over 28% of the internet. WordPress had its inception on May 27th, 2003, when Matt Mullenweg and Mike Little forked the b2/cafelog platform , originally written by Michel Valdrighi. But did you know that WordPress used to exist without plugins?

Herjavec Group
FEBRUARY 18, 2021
I was personally honored in my early career to work for Wang Laboratories and was invited to share one of my visions ‘fax over the internet’ with the company, which I invented. In 2003, he knew that firewalls were too complex for all IT staff and for understaffed companies to manage. Welcome to the information technology storm.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content