Pegasus spyware and how it exploited a WebP vulnerability
Malwarebytes
SEPTEMBER 27, 2023
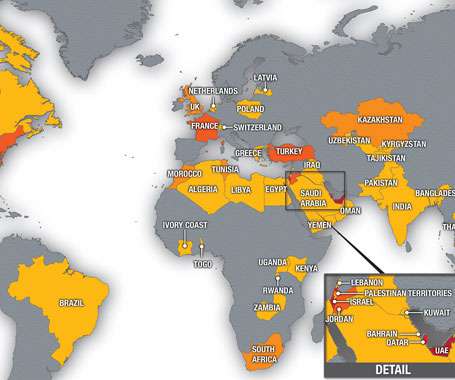
Recent events have demonstrated very clearly just how persistent and wide-spread the Pegasus spyware is. The exploit chain based on these vulnerabilities was capable of compromising devices without any interaction from the victim and were reportedly used by the NSO Group to deliver its infamous Pegasus spyware.



















Let's personalize your content