Unknown FinSpy Mac and Linux versions found in Egypt
Security Affairs
SEPTEMBER 27, 2020
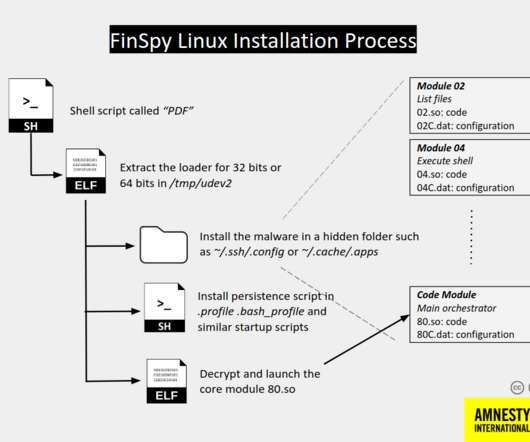
Experts from Amnesty International uncovered a surveillance campaign that targeted Egyptian civil society organizations with a new version of FinSpy spyware. Since 2011 it was employed in attacks aimed at Human Rights Defenders (HRDs) in many countries, including Bahrain, Ethiopia, UAE, and more.














Let's personalize your content