LimeRAT malware delivered using 8-year-old VelvetSweatshop trick
Security Affairs
APRIL 1, 2020
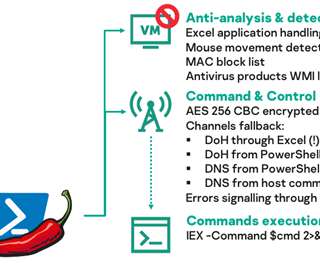
Researchers spotted a campaign using Excel files to spread LimeRAT malware using the 8-year-old and well-known VelvetSweatshop bug. Researchers at the Mimecast Threat Center spotted a new campaign using Excel files to spread LimeRAT malware using the 8-year-old VelvetSweatshop bug. ” reads the analysis published by the experts.



















Let's personalize your content