Devices from Dell, HP, and Lenovo used outdated OpenSSL versions
Security Affairs
NOVEMBER 25, 2022
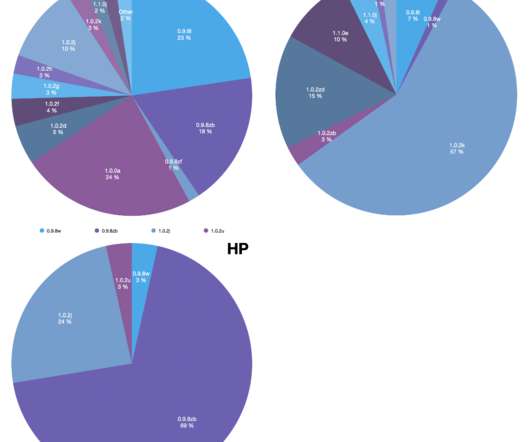
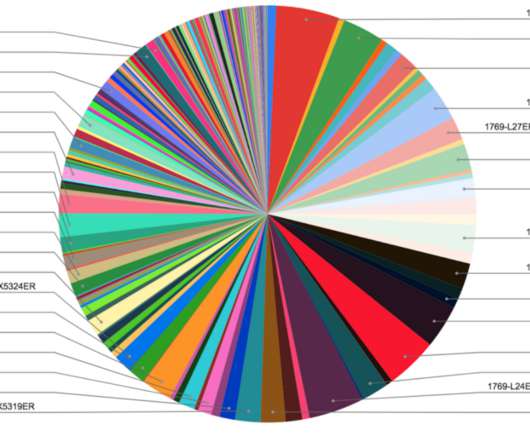
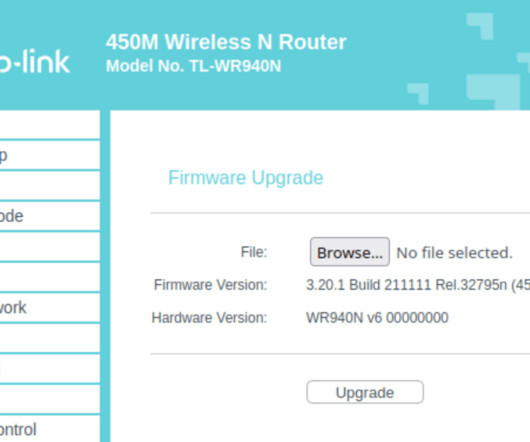
The researchers discovered the issue by analyzing firmware images used devices from the above manufacturers. The experts analyzed one of the core frameworks EDKII used as a part of any UEFI firmware which has its own submodule and wrapper over the OpenSSL library ( OpensslLib ) in the CryptoPkg component. that dates back 2012.













Let's personalize your content