Who’s Behind the Botnet-Based Service BHProxies?
Krebs on Security
FEBRUARY 24, 2023
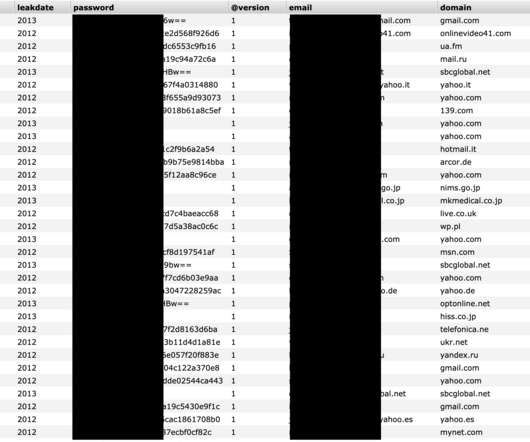
Last year, researchers at Minerva Labs spotted the botnet being used to blast out sextortion scams. BHProxies has authored 129 posts on Black Hat World since 2012, and their last post on the forum was in December 2022. The website BHProxies[.]com The account didn’t resume posting on the forum until April 2014. .”

















Let's personalize your content