Financially motivated Earth Lusca threat actors targets organizations worldwide
Security Affairs
JANUARY 18, 2022
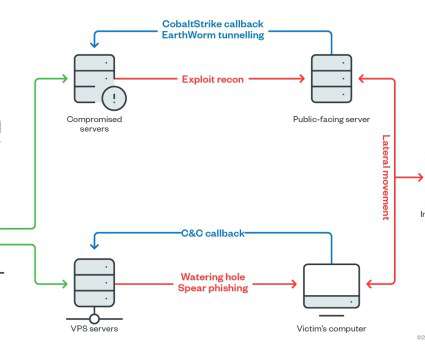
The Winnti group was first spotted by Kaspersky in 2013, but according to the researchers the gang has been active since 2007. ” The threat actors were observed deploying Cobalt Strike in the infected networks, along with a set of additional malware and web shells. ” Follow me on Twitter: @securityaffairs and Facebook.














Let's personalize your content