Bomb Threat, Sextortion Spammers Abused Weakness at GoDaddy.com
Krebs on Security
JANUARY 22, 2019
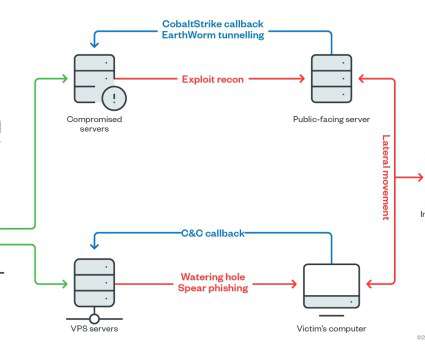
Your Web browser knows how to find a Web site name like example.com thanks to the global Domain Name System (DNS), which serves as a kind of phone book for the Internet by translating human-friendly Web site names (example.com) into numeric Internet address that are easier for computers to manage. ” SAY WHAT? 13, 2018 bomb threat hoax.







































Let's personalize your content