Sextortion campaign uses Goontact spyware to target Android and iOS users
Security Affairs
DECEMBER 16, 2020
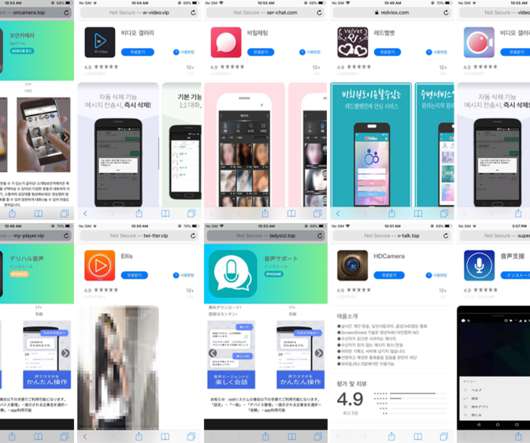
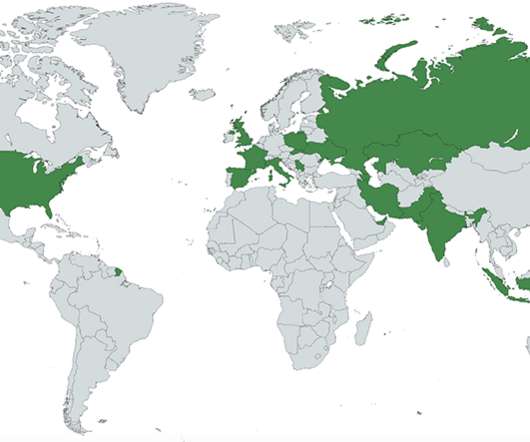
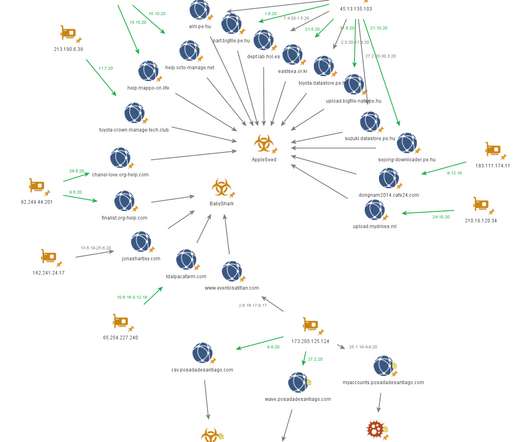
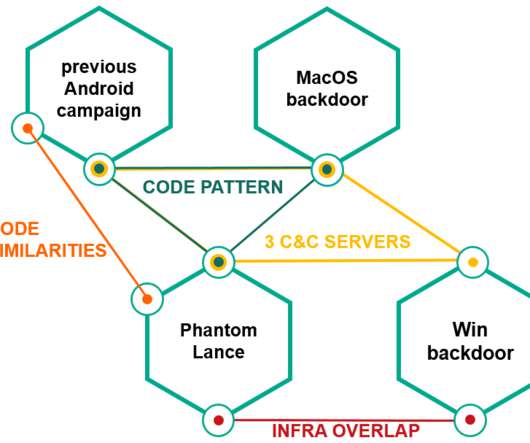
Security experts spotted a new malware strain, named Goontact, that allows its operators to spy on both Android and iOS users. Security researchers from Lookout have discovered new spyware, dubbed Goontcat, that could target both Android and iOS users. The spyware is likely used as part of a sextortion campaign.














Let's personalize your content