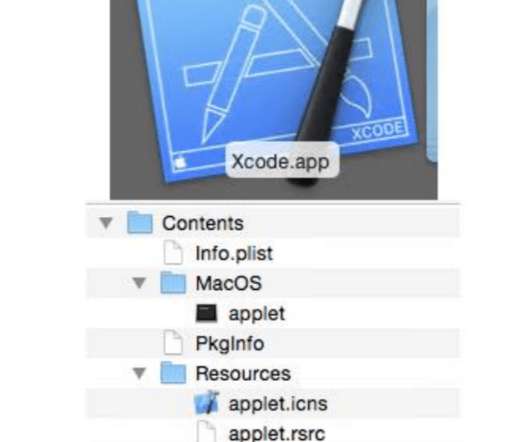
XCSSET Mac spyware spreads via Xcode Projects
Security Affairs
AUGUST 15, 2020
The malware also implements ransomware behavior, it is able to encrypt files and display a ransom note. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->. Xcode developers are at risk. Pierluigi Paganini.



















Let's personalize your content