New GTPDOOR backdoor is designed to target telecom carrier networks
Security Affairs
MARCH 4, 2024
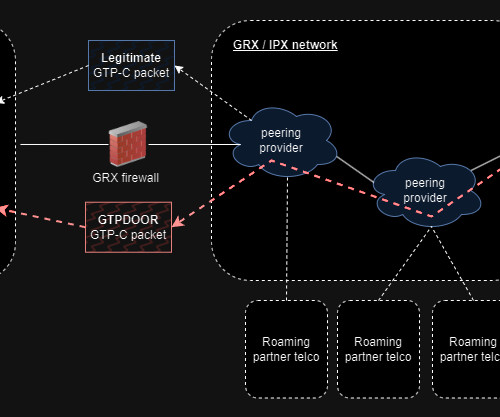
Researcher HaxRob discovered a previously undetected Linux backdoor named GTPDOOR, designed to target telecom carrier networks. Security researcher HaxRob discovered a previously undetected Linux backdoor dubbed GTPDOOR, which is specifically crafted to carry out stealth cyber operations within mobile carrier networks.



























Let's personalize your content