Feds Warn About Critical Infrastructure Ransomware Attacks, Vulnerabilities
eSecurity Planet
FEBRUARY 15, 2022
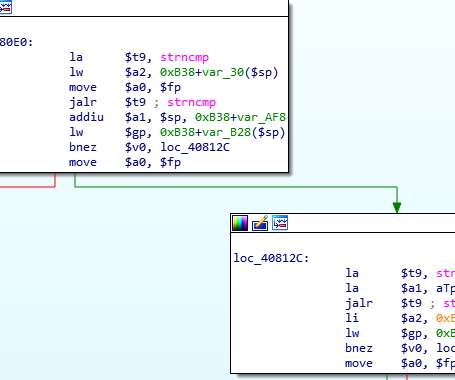
The ransomware encrypts files on compromised Windows host systems, including physical and virtual servers, the advisory noted, and the executable leaves a ransom note in all directories where encryption occurs, including ransom payment instructions for obtaining a decryption key.






















Let's personalize your content