New Triada Trojan comes preinstalled on Android devices
Security Affairs
APRIL 2, 2025
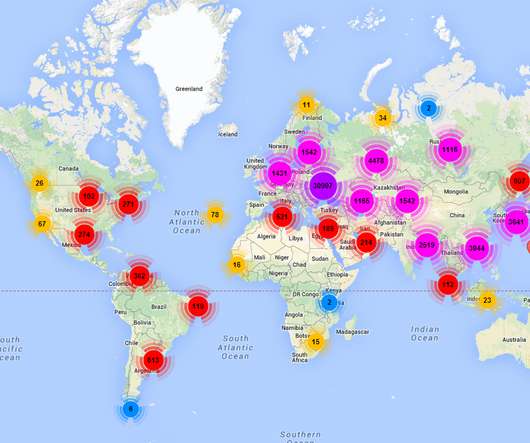
Judging by the analysis of transactions, they were able to transfer about $270,000 in various cryptocurrencies to their crypto wallets.” “However, in reality, this amount may be larger; the attackers also targeted Monero, a cryptocurrency that is untraceable.”




































Let's personalize your content