DDoS attacks in Q3 2021
SecureList
NOVEMBER 8, 2021
Q3 2021 brought two new DDoS attack vectors, potentially posing a serious threat, including for major web resources. ris , a new botnet capable of carrying out powerful DDoS attacks. For instance, a DDoS attack on a Cloudflare customer (attributed to M?ris) We won't let our #DDoS stop us doing what we love!



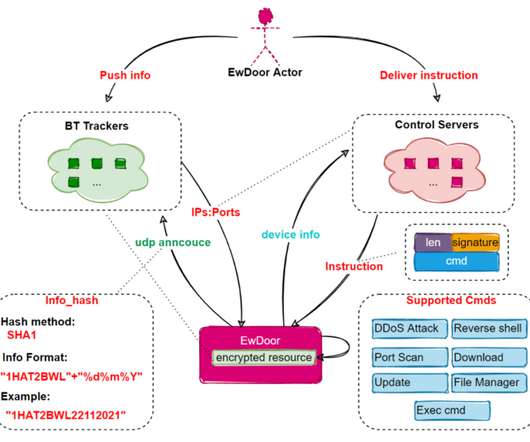
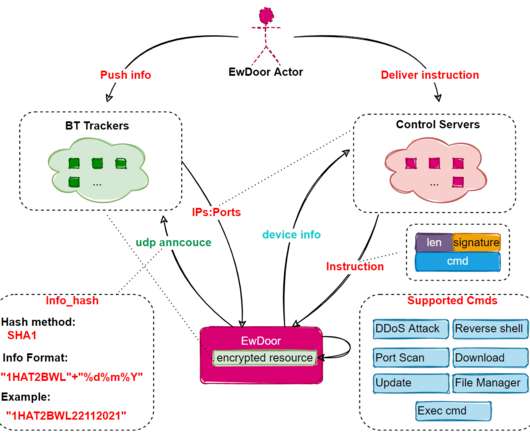
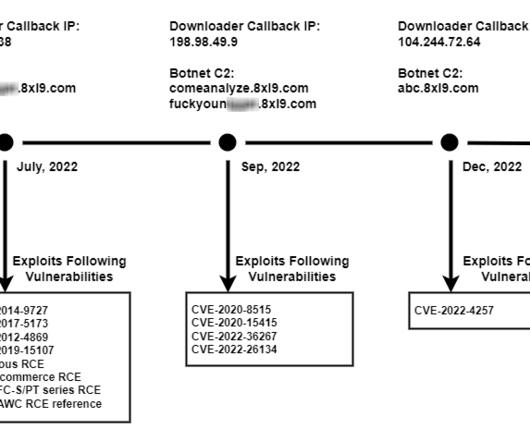







































Let's personalize your content