APT C-23 group targets Middle East with an enhanced Android spyware variant
Security Affairs
NOVEMBER 26, 2021
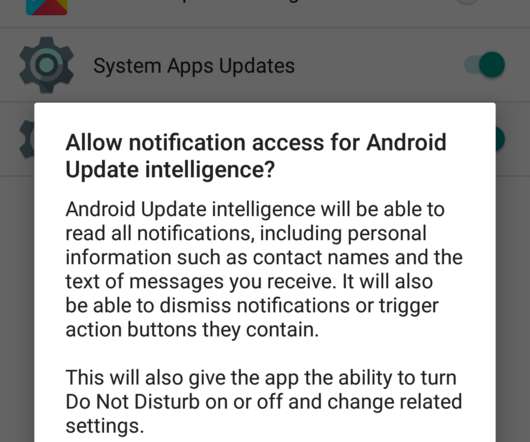
A threat actor, tracked as APT C-23, is using new powerful Android spyware in attacks aimed at targets in the Middle East. The APT C-23 cyberespionage group (also known as GnatSpy, FrozenCell, or VAMP) continues to target entities in the Middle East with enhanced Android spyware masqueraded as seemingly harmless app updates (i.e.
































Let's personalize your content