Norton 360 Now Comes With a Cryptominer
Krebs on Security
JANUARY 6, 2022
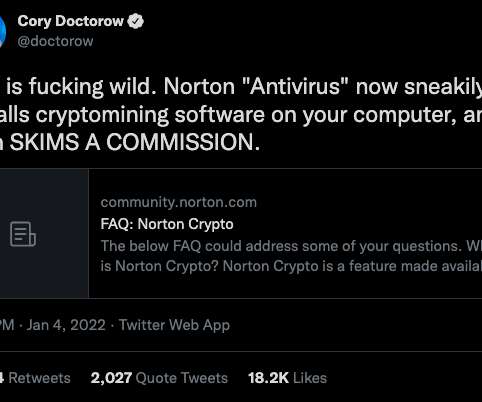
Norton 360 , one of the most popular antivirus products on the market today, has installed a cryptocurrency mining program on its customers’ computers. which was renamed to NortonLifeLock in 2019 (LifeLock is now included in the Norton 360 service). Only you have access to the wallet.”




























Let's personalize your content