Godlua backdoor, the first malware that abuses the DNS over HTTPS (DoH)
Security Affairs
JULY 4, 2019
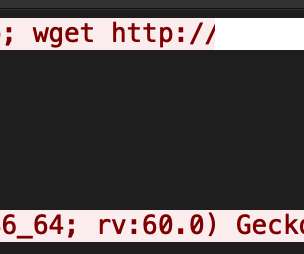
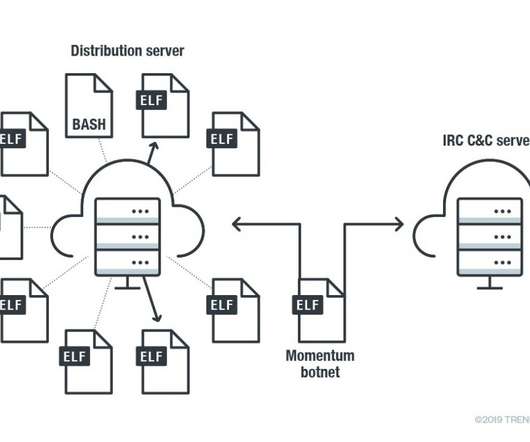
The peculiarity of this new piece of malware is the ability to communicate with C2 servers via DNS over HTTPS ( DoH ). The DoH protocol was a new standard proposed in October 2018 and it is currently supported by several publicly available DNS servers. com domain. ” states the analysis. ” states the analysis.
































Let's personalize your content