Ransomware en masse on the wane: top threats inside web-phishing in H1 2020
Security Affairs
SEPTEMBER 18, 2020
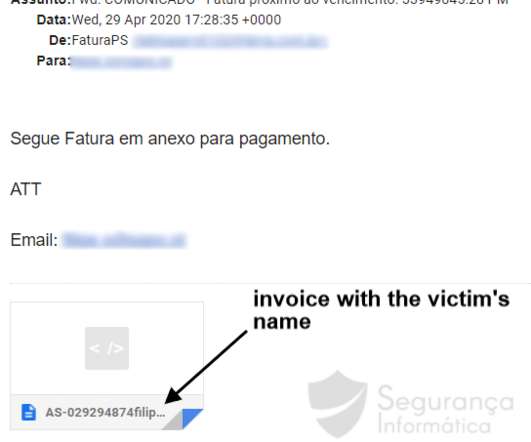
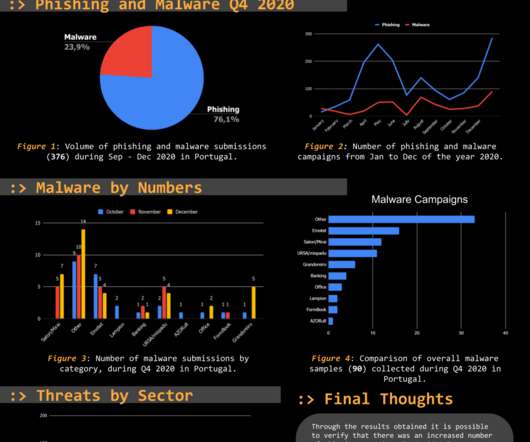
Web-phishing targeting various online services almost doubled during the COVID-19 pandemic , it accounted for 46 percent of the total number of fake web pages. Secure web- phishing. In the first six months of 2020, CERT-GIB blocked a total of 9 304 phishing web resources, which is an increase of 9 percent compared to the previous year.


















Let's personalize your content