Cybersecurity in Aviation: Rising Threats and Modernization Efforts
SecureWorld News
JUNE 9, 2025
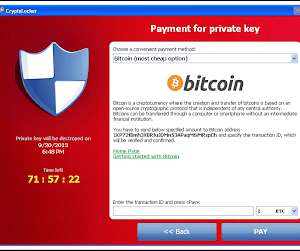
Global data reveals that cyberattacks rose by 131% between 2022 and 2023 across the aviation industry, with a 74 percent increase since 2020, underscoring the profundity of this threat. There has been an alarming surge in cyberattacks against airlines, airports, and air traffic management systems.

































Let's personalize your content