Web Hacking Service ‘Araneida’ Tied to Turkish IT Firm
Krebs on Security
DECEMBER 19, 2024
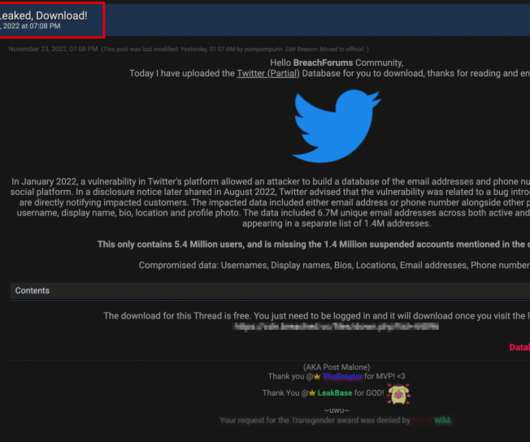
The makers of Acunetix, Texas-based application security vendor Invicti Security , confirmed Silent Push’s findings, saying someone had figured out how to crack the free trial version of the software so that it runs without a valid license key. Archive.org’s recollection of what altugsara dot com looked like in 2021.









































Let's personalize your content