2021 Threat Intelligence Use Cases
Anton on Security
MARCH 19, 2021
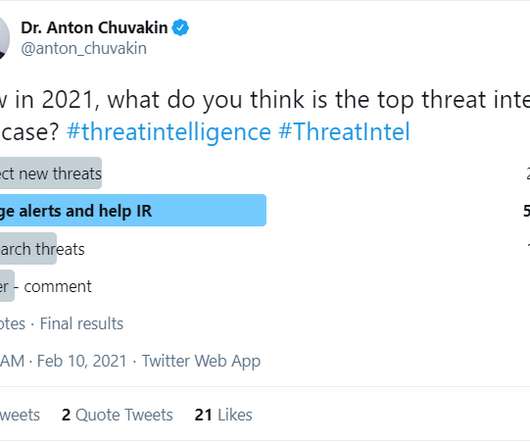
For a reason that shall remain nameless, I’ve run this quick poll focused on the use cases for threat intelligence in 2021. Antons Threat Intel Poll 2021 Here are some thoughts and learnings based on the poll and the discussion , as well as other things. The question and the results are below.













































Let's personalize your content