SOC 2025: Making Sense of Security Data
Security Boulevard
FEBRUARY 8, 2022
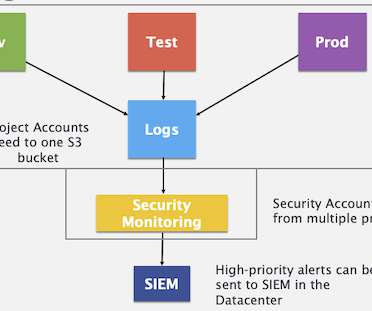
As we consider what the SOC will look like in 2025 , given the changing attack surface and available skills base, we’ve got to face reality. These sources include logs and alerts from your firewalls, IPSs, web proxies, email gateways, DLP systems, identity stores, etc. Mike Rothman. (0) 0) Comments. Subscribe to our daily email digest.







































Let's personalize your content