SOC 2025: Detection/Analytics
Security Boulevard
MARCH 10, 2022
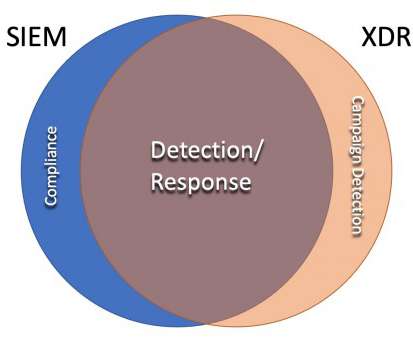
It turns out analytics aren’t a separate thing; they are part of every security thing. That’s right, analytics drive endpoint security offerings. Cloud security products? Network security detection? You already have security monitoring technology, which you probably don’t want to (or can’t) forklift.

























Let's personalize your content