Italy announced its National Cybersecurity Strategy 2022/26
Security Affairs
MAY 26, 2022
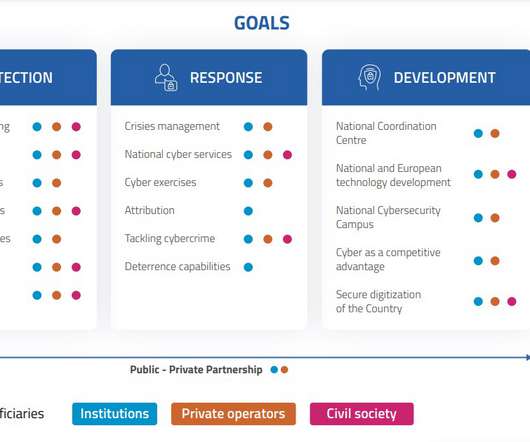
Italy announced its National Cybersecurity Strategy for 2022/26, a crucial document to address cyber threats and increase the resilience of the country. Preventing online disinformation in a broader context of the hybrid threat; Management of cyber crises; National and European strategic digital sector autonomy.

















Let's personalize your content