Norton 360 Now Comes With a Cryptominer
Krebs on Security
JANUARY 6, 2022
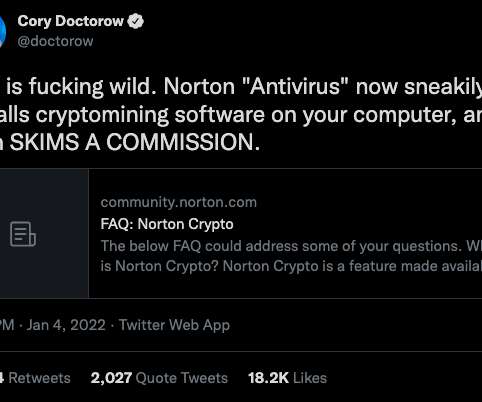
Norton 360 , one of the most popular antivirus products on the market today, has installed a cryptocurrency mining program on its customers’ computers. According to the FAQ posted on its site , “ Norton Crypto ” will mine Ethereum (ETH) cryptocurrency while the customer’s computer is idle.







































Let's personalize your content