Microsoft Defender can now protect servers against ProxyLogon attacks
Security Affairs
MARCH 21, 2021
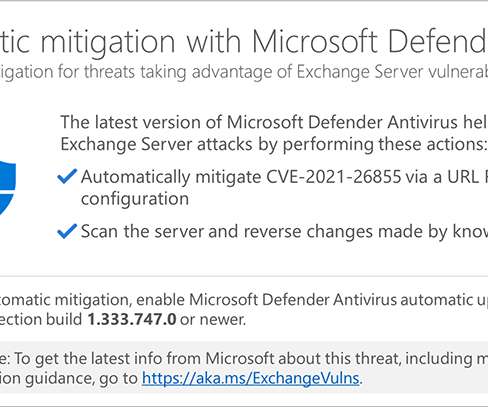
Microsoft announced that its Defender Antivirus and System Center Endpoint Protection now protects users against attacks exploiting Exchange Server vulnerabilities. “Today, we have taken an additional step to further support our customers who are still vulnerable and have not yet implemented the complete security update. .

































Let's personalize your content