Architecture Matters When it Comes to SSE
CyberSecurity Insiders
MAY 17, 2023
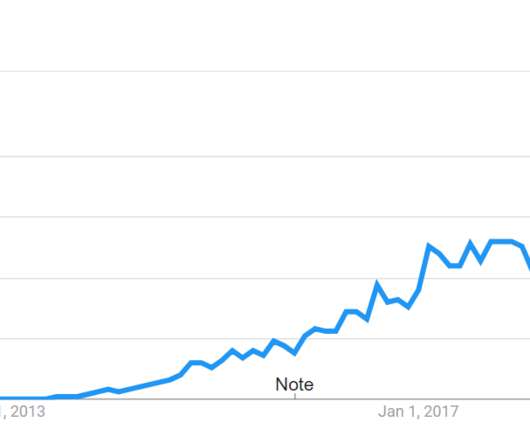
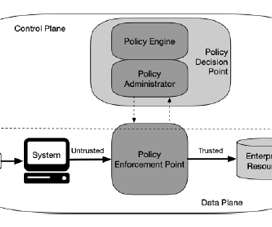
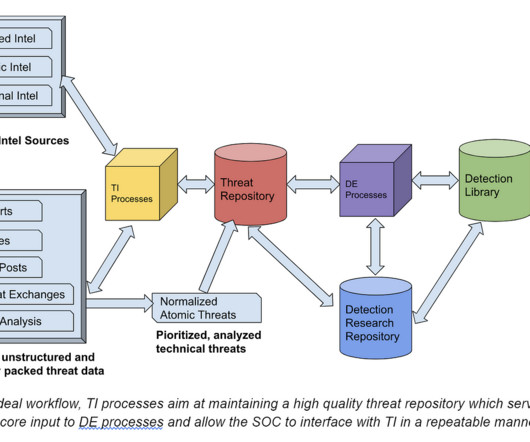
” Or said another way, “architecture matters”. Application performance and security must be accounted for. If so, I need to account for this and the result may be that I need to add my own interconnects into Azure or similar services. One which puts the network/security engineer back in the driver’s seat.








































Let's personalize your content