How Your Organization Can Prevent Account Takeover
Security Boulevard
JUNE 7, 2022
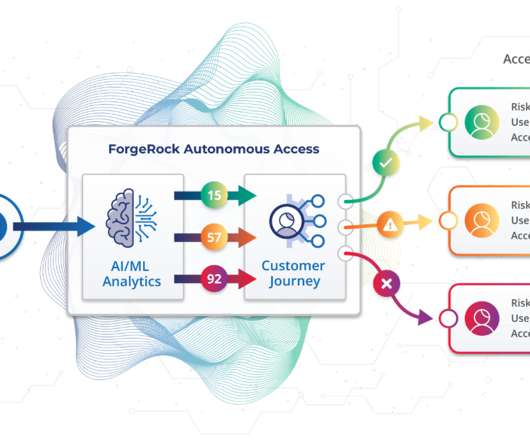
Though the tools and technologies have improved enormously in the last couple of decades, enterprises remain under attack. As people conduct more and more business online — both in their personal and professional lives — cybercrime has become big business, more organized and well-funded than ever. Why ForgeRock Autonomous Access?











































Let's personalize your content