FBI Warns of Cyber Attacks on Multi-Factor Authentication
Adam Levin
OCTOBER 8, 2019
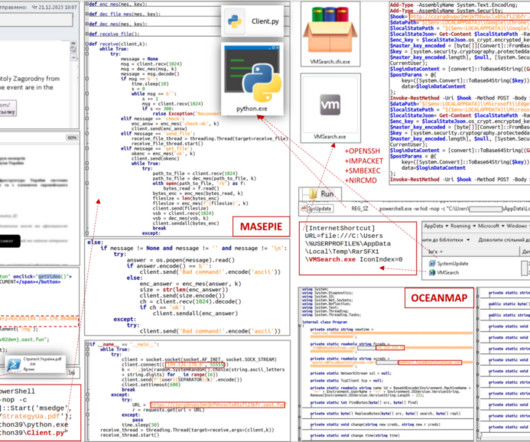
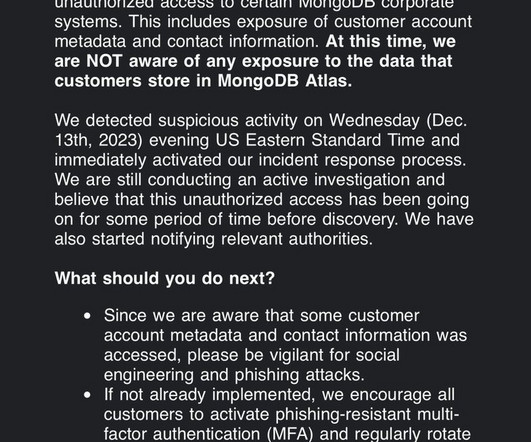
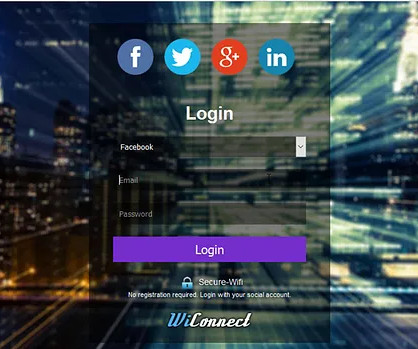
The methods used were SIM swapping , phishing , and newer hacking tools such as Muraena and Necrobrowser. of attacks on businesses. . The post FBI Warns of Cyber Attacks on Multi-Factor Authentication appeared first on Adam Levin. Read the PIN here.














































Let's personalize your content