Ukraine warns of attacks aimed at taking over Telegram accounts
Security Affairs
APRIL 6, 2022
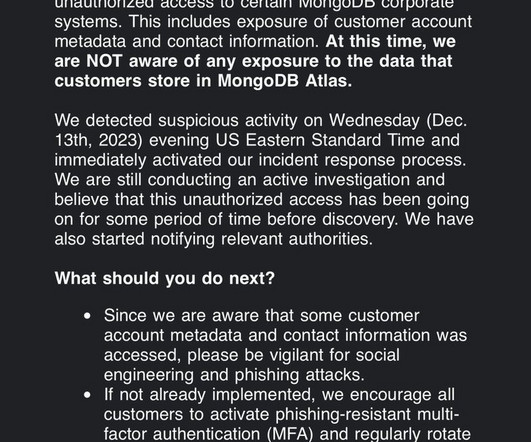
Ukraine’s technical security and intelligence service warns of threat actors targeting aimed at gaining access to users’ Telegram accounts. State Service of Special Communication and Information Protection (SSSCIP) of Ukraine spotted a new wave of cyber attacks aimed at gaining access to users’ Telegram accounts.














































Let's personalize your content