Raspberry Robin malware used in attacks against Telecom and Governments
Security Affairs
DECEMBER 24, 2022
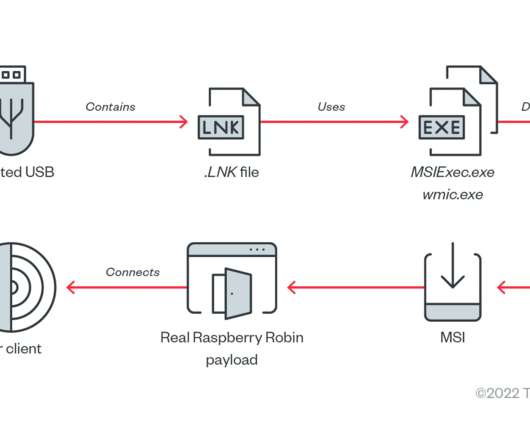
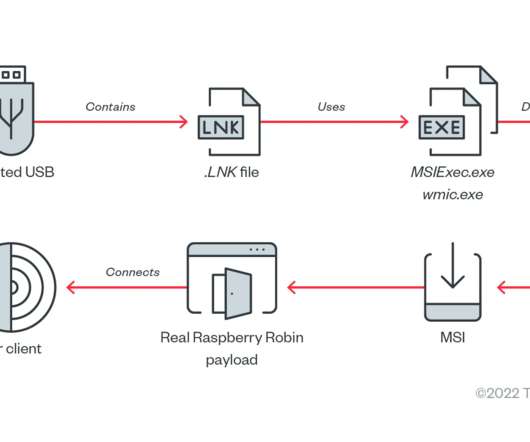
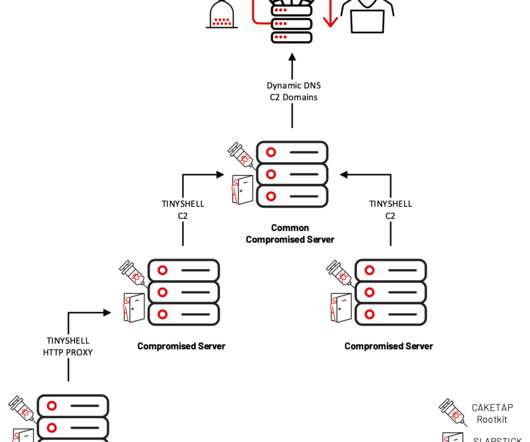
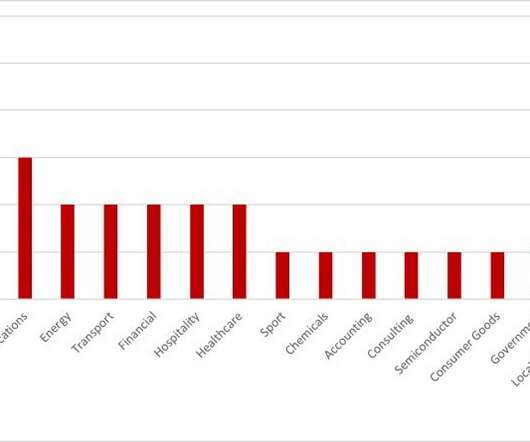
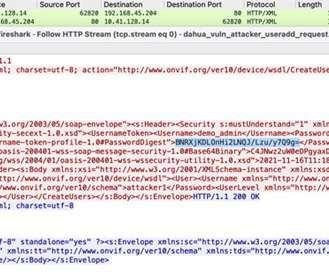
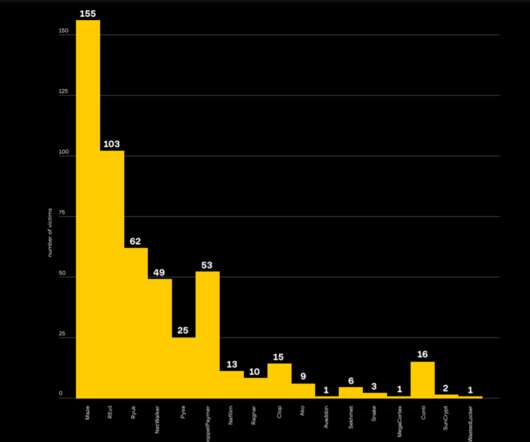
The Raspberry Robin worm attacks aimed at telecommunications and government office systems across Latin America, Australia, and Europe. Researchers from Trend Micro have uncovered a Raspberry Robin worm campaign targeting telecommunications and government office systems across Latin America, Australia, and Europe.



































Let's personalize your content