YouTube creators’ accounts hijacked with cookie-stealing malware
Security Affairs
OCTOBER 20, 2021
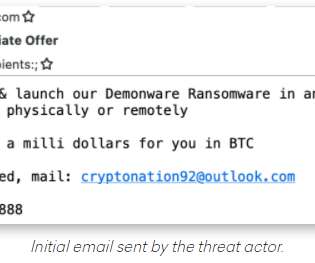
A Cookie Theft malware was employed in phishing attacks against YouTube creators, Google’s Threat Analysis Group (TAG) warns. Financially motivated threat actors are using Cookie Theft malware in phishing attacks against YouTube creators since late 2019. Below are the job descriptions used to recruit the hackers.
















































Let's personalize your content