Social Engineering from the Attacker Perspective
Security Through Education
FEBRUARY 9, 2022
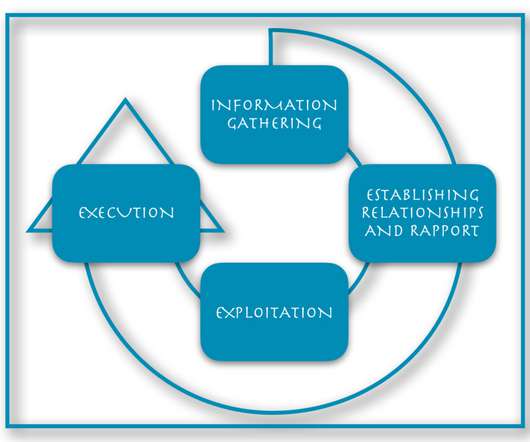
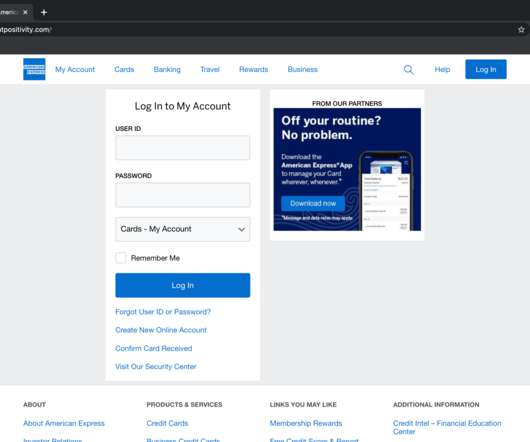
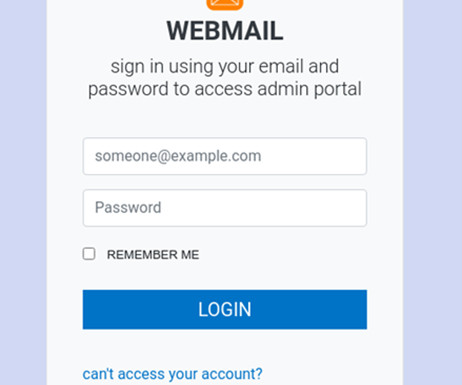
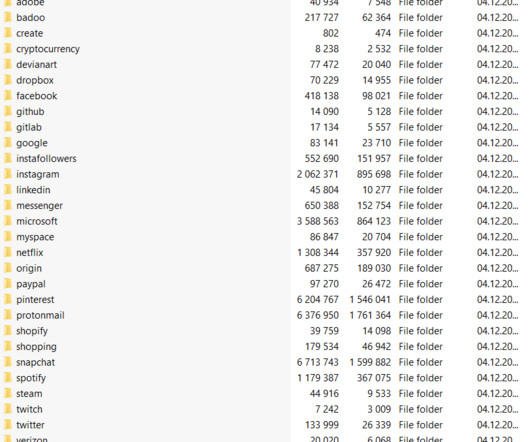
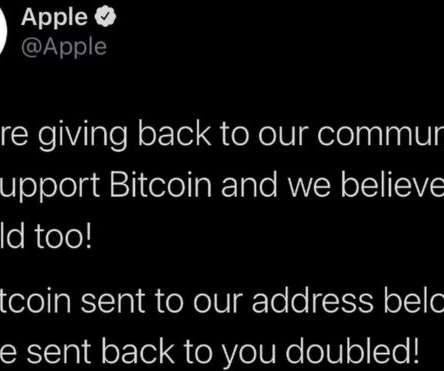
At Social-Engineer, LLC (SECOM), we define social engineering as “any act that influences a person to take an action that may or may not be in their best interest.” If you Google “social engineering,” you will get a very different and more negative definition. billion to phone scams.































Let's personalize your content